
Shield Platform Encryption
Shield Platform Encryption can help you keep the information in your Salesforce org safe and secure. We can encrypt all kinds of data. Phone numbers, dates, names, text files, images, you name it. If it’s recorded digitally, we can encrypt it. Shield Platform Encryption encrypts data at rest, meaning that we encrypt it when it’s being stored within Salesforce.
Generally in salesforce, we use FLS and Authorization techniques to secure data but to go an extra mile shield encryption will be used.
Salesforce offers you two ways to encrypt data. Classic encryption is included in the base price of your Salesforce license. With classic encryption, you can protect a special type of custom text field that you create for data you want to encrypt. The custom field is protected with industry-standard 128-bit Advanced Encryption Standard (AES) keys.
How to Turn on Shield Platform Encryption
1. Provision your license.
Contact Salesforce to get one. Shield Platform Encryption is automatically available in Developer Edition orgs created on or after the Summer of 2015.
2. Assign permissions.
To enable Shield Platform Encryption, you need the Customize Application and Manage Encryption Keys permissions. After you enable encryption, you can give others permission to complete administration tasks on the Encryption Policy page. However, you likely don’t want everyone managing encryption keys. Assign permissions with these scenarios in mind.
For example, as an admin, assign yourself the View Setup and Configuration permission. This lets you enable encryption features for fields, files, attachments, and apps.
3. Enable Shield Platform Encryption for your org.
When you have your license and permissions set up, you can enable Shield Platform Encryption on your orgs. You then create org-specific tenant secrets and customize your encryption settings for each org.
Assign Permissions and Create a Tenant Secret
- From Setup, enter Permission Sets in the Quick Find box, then select Permission Sets.
- Click New.
- Create a label for the set of permissions, for example, Key Manager. The API name populates with a variation of your chosen label.
- Click Save.
- In the System section of the Key Manager page, select System Permissions.
- Click Edit, and enable the Customize Application and Manage Encryption Keys permissions.
- Click Save.
- From Setup, enter Users in the Quick Find box, then select Users.
- Select the name you want in the User list (in this case, that’s yours).
- Scroll down to Permission Set Assignments, and select Edit Assignments.
- Select Key Manager, then add it to the Enabled Permission Sets list.
- Click Save.
Generate a Tenant Secret( Key Management)
Before you can start encrypting patient data, you’ll need to create a tenant secret.
- From Setup, in the Quick Find box, enter Platform Encryption, and then select Key Management.
- Select Data in Salesforce from the Choose Tenant Secret Type list. Tenant secret types allow you to specify which kind of data you want to encrypt with a tenant secret. We’ll start by encrypting data in the core Salesforce database for now.
- Select Generate Tenant Secret.

Generating a new tenant secret and archiving the old one is called key rotation, because your new tenant secret generates new encryption keys. Your organization’s regulatory bodies and security policies often recommend that you rotate your tenant secrets (and keys) at specific intervals.
You can update your tenant secret in just a few steps.
- From Setup, in the Quick Find box, enter Platform Encryption, and then select Key Management.
The Status column in the Key Management view identifies tenant secrets as either Active, Archived, or Destroyed.
- Select a tenant secret type from the list.
- To generate a new tenant secret, click Generate Tenant Secret. This action archives the previously active tenant secret of that type.
Archived tenant secrets can’t encrypt new data, but the app uses these archived keys to decrypt the data that was previously encrypted with it.

Encrypt Standard Fields (Encryption Policy)
Now that you have an active tenant secret, you can start encrypting data, which might include standard fields, like Description and Email, or custom Text fields.
- From Setup, in the Quick Find box, enter Platform Encryption, and then select Encryption Policy.
- Select Encrypt Fields.
- Click Edit.
- Select the fields you want to encrypt, and click Save.

The automatic validation process checks all your org settings and sends you an email. If any settings block or prevent encryption, you receive instructions for fixing them.
Note: encryption doesn’t take the place of field-level access controls.
Encrypt Files and Attachments
You’ve done your homework and know how to help Doc: file and attachment encryption.
- From Setup, in the Quick Find box, enter Platform Encryption, and then select Encryption Policy.
- Select Encrypt Files and Attachments.
- Click Save.

Encryption Statistics and Data Sync

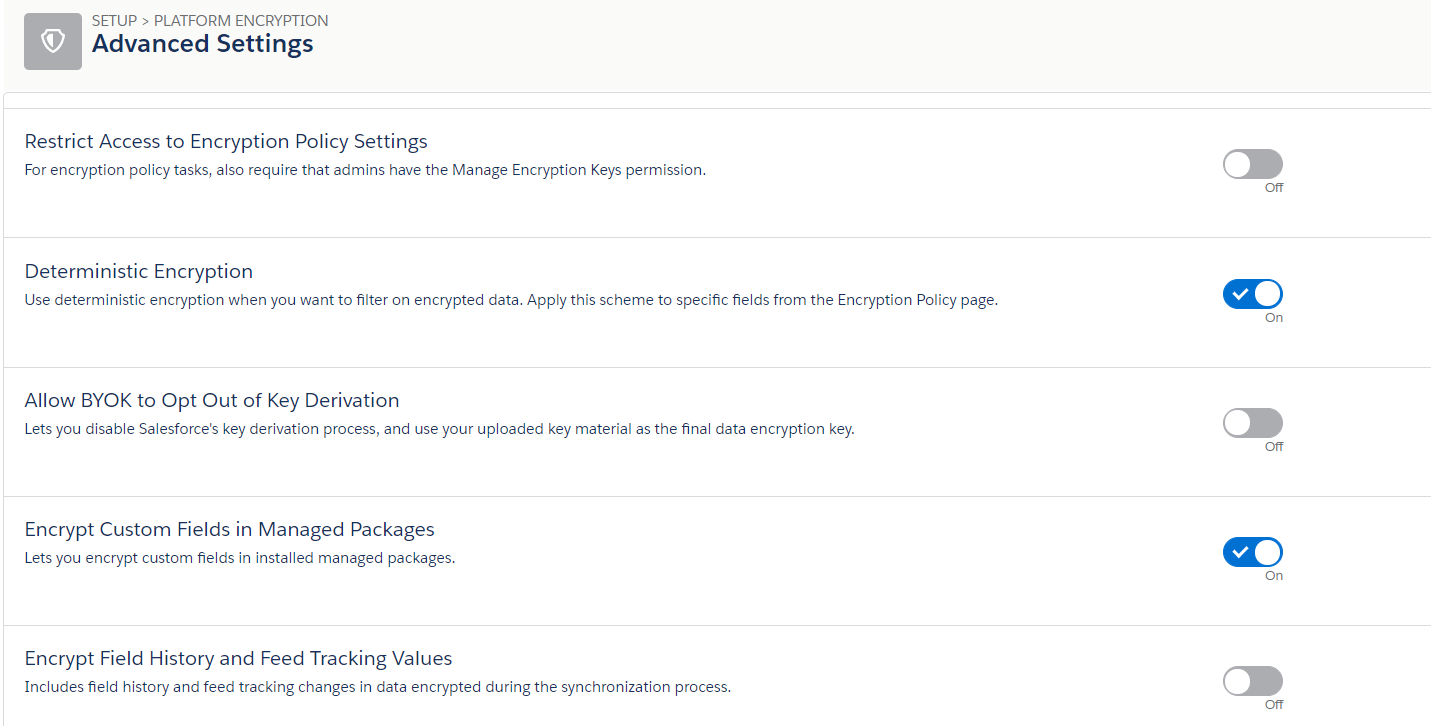
Restrict Access to Encryption Policy Settings
For encryption policy tasks, also require that admins have the Manage Encryption Keys permission.
- Deterministic Encryption
Use deterministic encryption when you want to filter encrypted data. Apply this scheme to specific fields from the Encryption Policy page.
- Allow BYOK to Opt Out of Key Derivation
You disable Salesforce’s key derivation process and use your uploaded key material as the final data encryption key.
- Encrypt Custom Fields in Managed Packages
Let’s encrypt custom fields in installed managed packages.
- Encrypt Field History and Feed Tracking Values
Includes field history and feed tracking changes in data encrypted during the synchronization process.
Shield Platform Encryption Best Practices
- Define a threat model for your organization.
To identify the most likely threats to affect your organization, walk through a formal threat modeling exercise. Use your findings to create a data classification scheme, which can help you decide what data to encrypt.
- Encrypt only where necessary.
- Not all data is sensitive. Focus on information that requires encryption to meet your regulatory, security, compliance, and privacy requirements. Unnecessarily encrypting data impacts functionality and performance.
- Evaluate your data classification scheme early and work with stakeholders in security, compliance, and business IT departments to define requirements. Balance business-critical functionality against security and risk measures and challenge your assumptions periodically.
- Create a strategy early for backing up and archiving keys and data.
If your tenant secrets are destroyed, reimport them to access your data. You are solely responsible for making sure that your data and tenant secrets are backed up and stored in a safe place. Salesforce cannot help you with deleted, destroyed, or misplaced tenant secrets.
- Read the Shield Platform Encryption considerations and understand their implications on your organization.
- Evaluate the impact of the considerations on your business solution and implementation.
- Test Shield Platform Encryption in a sandbox environment before deploying to a production environment. Encryption policy settings can be deployed using changesets.
- Before enabling encryption, fix any violations that you uncover. For example, if you reference encrypted fields in a SOQL ORDER BY clause, a violation occurs. Fix the violation by removing references to the encrypted fields.
- When requesting feature enablement, such as pilot features, give Salesforce Customer Support several days lead time. The time to complete the process varies based on the feature and how your org is configured.
- Analyze and test AppExchange apps before deploying them.
- If you use an app from the AppExchange, test how it interacts with encrypted data in your organization and evaluate whether its functionality is affected.
- If an app interacts with encrypted data that’s stored outside of Salesforce, investigate how and where data processing occurs and how information is protected.
- If you suspect Shield Platform Encryption could affect the functionality of an app, ask the provider for help with evaluation. Also, discuss any custom solutions that must be compatible with Shield Platform Encryption.
- Apps on the AppExchange that are built exclusively using Lightning Platform inherit Shield Platform Encryption capabilities and limitations.
- Use out-of-the-box security tools.
Shield Platform Encryption is not a user authentication or authorization tool. To control which users can see which data, use out-of-the-box tools such as field-level security settings, page layout settings, and sharing rules, rather than Shield Platform Encryption.
- Grant the Manage Encryption Keys user permission to authorized users only.
Users with the Manage Encryption Keys permission can generate, export, import, and destroy organization-specific keys. Monitor the key management activities of these users regularly with the setup audit trail. - Synchronize your existing data with your active key material.
Existing field and file data are not automatically encrypted when you turn on Shield Platform Encryption. To encrypt existing field data, update the records associated with the field data. This action triggers encryption for these records so that your existing data is encrypted at rest. To encrypt existing files or get help updating other encrypted data, contact Salesforce. We can encrypt existing file data in the background to ensure data alignment with the latest encryption policy and key material.
When you contact Salesforce support to request the background encryption service, allow at least a week before you need the background encryption completed. The time to complete the process varies based on the volume of data involved. It could take several days.
Field Limits with Shield Platform Encryption
Under certain conditions, encrypting a field can impose limits on the values that you store in that field.

And Salesforce features work as expected when you work with data that’s encrypted with Shield Platform Encryption.
- Connect Offline
- Commerce Cloud (Salesforce B2B Commerce version 4.10 and later is supported)
- Data.com
- Einstein Engine
- Heroku (but Heroku Connect does support encrypted data)
- Marketing Cloud (but Marketing Cloud Connect does support encrypted data)
- Salesforce CPQ
- Salesforce IQ
- Social Customer Service
- Thunder
- Quip
- Salesforce Billing
Thanks for Reading..